Senior Engineer, Network Design, Strategy, and Cybersecurity
Proactive solutions for securing environment while bringing value to business by reducing downtime, saving costs, and automating what can be done to improve overall business fuctions.
Passion for Technology and Continuous Learning
Security is an Ubiquitous Area of Technology, Where to Start?
NIST CyberSecurity Framework (CSF) 2.0
Cybersecurity Checklist - 2024
Risk Assessment
Policy Management
Data Protection
Identity and Access Management
Endpoint Security
Network Security
Compliance and Legal Requirements
Update Security Policies
Employee Training
Third-Party and Vendor Management
Incident Response Planning
Emerging Technologies and Trends
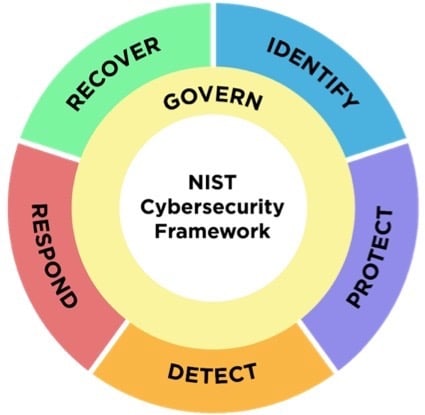
What is it? A Framework for managing security risks on a continuous bases. It is comprised with six functions are depicted in the image on the right.
Risk needs to be defined with understanding of how much TOLERANCE an organization is willing to take for a security risk. It is Identifiying what needs to be secured and implementing the security controls.
Example: This Strategic Framework is used as a bases for AWS Cloud Security. However, they are not on the newest release of NIST SP 800-61r3. They have not incorporated Govern yet. https://aws.amazon.com/security/
Start with a Framework such as NIST - National Institute of Standards and Technology, from the US Department of Commerce. Understand the Framework, Risk Management, and Knowledge of the CIA Triad
NIST Incident Response - NIST SP 800-61r3 - framework is preparation for security using the following: Govern, Identify, and Protect; then the Life Cycle is to Detect, Respond, and Recover.
Cybersecurity First Principles: A Reboot of Strategy and Tactics - Rick Howard
I first met Rick in a University of Washington Class as he was a guest speaker, he spoke with confidence and knowledge.
His book is revolutionary when it comes to where do we start with security. Such as when we thought that having secure passwords, a firewall on the network, Intrusion Detection\Intrusion Protection with defense in depth was enough. This goes deeper into the knowledge of starting in the right place to secure your environment.
Security Starts with Understanding What Needs To Be Secured and Do What is Necessary to Prevent a Cybersecurity Incident.
The First Principle: "Reduce the Probability of Material Impact Due to a Cyber Event in the Next Three Years" (Rick Howard)
Material Impact is to use strategies and tactics that drive down material impact over a defined amount of time. First Strategy: Passive Cyber Hygiene, in other words, Zero Trust.
Second Strategy: Active Defenses (drive down Intrusion Kill Chain. Intrusion Kill Chain theory is identify what a hacker needs to do to achieve their goal of breaking into your systems).
Third Strategy: Building Resilience
Fourth Strategy: Risk Forecasting
Fifth Strategy: Automation in all areas of the network, applications, systems, and services where it is safe to automate.


CIA Triad - Confidentiality, Integrity, Availability
The CIA triad is Confidentiality, Integrity, and Availability where confidentiality is to protect data, Integrity is to keep it accurate, and Availability is to have the data where you can retrieve it and have it when you need it.
Confidentiality > Implementing Security Controls to address Risks and Vulnerabilities based on the Threat it may pose. The Goal is to prevent or minimize the impacts of an incident.
Countermeasures for Confidentiality: Encryption, Network Traffic Padding, Rigorous Authentication Procedures, Data Classification, Strick Access Controls, Training, Hiding or Preventing Disclosure of Data.
Integrity > Ensure reliability and consistency of data. The data must be Accurate, and valid. It is to allow authorized users or applications to make changes to data and keep unauthorized users from making modifications.
Countermeasures: Access Control, Authentication Procedures, Checksums, Version Control, and Continuous Authentication Verified.
Availability > Objects and resources are granted uninterrupted access to objects. Availability is subject to DoS and Buffer overflows.
Countermeasures: Robust design of coding practices, and systems configured with proper access controls.
CIA Triad is fundamental to securing an environment, however, it is not fully sufficient alone, for there is a plethora of security concepts and principles. This includes Authenticity, and Authentication, Authorization, and Accounting, (AAA). Plus Nonrepudiation.
Artificial Intelligence = AI - Besides Deep Fakes, or misinformation, what will happen when AI influences our decisions on who to vote for in an election? AI is fed data, it will do that which has been done before based on the data it analyzes. AI can be used to empower us and not take over our independent thinking. It can be used as a log aggregator to find those behaviors that indicate a cyber event.
Zero Trust
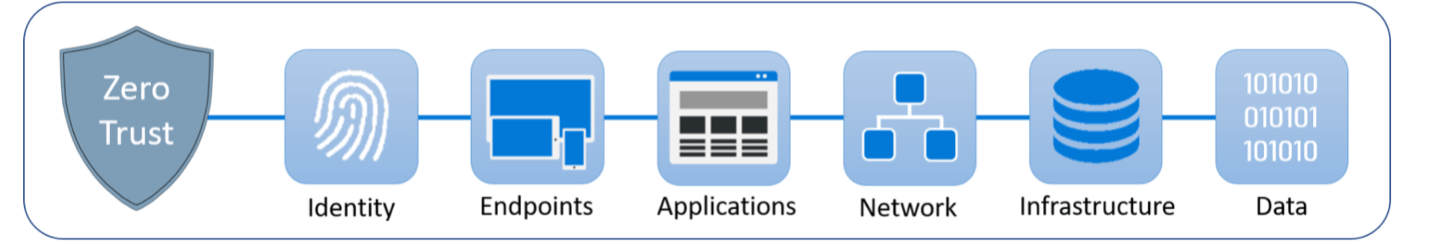
Zero Trust is a security framework that involves all users internal and external to the company to be authenticated, then authorized to the resources they are specifically required to access due to their needs. Zero Trust is to secure the network, data, applications, devices, and services that are used to conduct business. It should be in aligned with NIST 800-207 standards. The goal is to limit the impacts of a breach to a small area of the environment. The emphasis is on understanding there is a breach or could happen soon and that everything needs to be validated. Prevention of vulnerabilities involves log collection along with an aggregation tool to watch for abnormal behaviors. AI would be best suited for analysis of logging data if it is properly setup.
Cybersecurity VS. Information Security:
Cybersecurity :
Application
Cloud
Critical Infrastructure
Network
Information Security :
Access Controls
Compliance
Personal Controls
Technical Controls
Working in Technology is an interest and a passion.
Engineer with expertise in design & strategy, focusing on proactive solutions and value.
Self-Motivated
I strive to bring Improvements to the business.
Education
University of Washington - 5/2024
Professional & Continuing Eduction in Cybersecurity - Focus on Fundamentals of Security, Tools, Solutions, and Planning
Colorado Technical University
Hands On Tasks
VPN
Firewall including staging, rule updates, static routes, and resolution of rule hides from INSPEC engine
Load Balaners [A10 - F5]
Certificate Management and Deployment [PKI]
S64 and Infoblox - DNS
IAM
IDS/IPS
Windows Server Environments - Exchange Servers
Linux, MAC, Unix
JIRA
Splunk
Install, configure, updates, and support for hardware and software.
VMware
PCI, SOX, HIPAA
Proxy - WAF
Monitoring Centralized Syslog Servers
CyberArk
SDLC, ITIL
Sharepoint
Technical Writing
Leadership
Facilitation of Security Incidents
Coached Programmers and Level 4 Tech Support to Solutions to Mitigate Issues.
Designed and implemented security solutions in response to requirements.
Recommendations for hardware software
Security Incident Response
Problem Management Determination, tracking, and implementation of fixes.
CIA - Confidentiality, Integrity, Availability
Bachelor of Science in Information Technology and Software Engineering - 2023
Attributes
Problem Solving
Creative
Compassion for Fairness
Sense of Humor
Perseverence
Keen Sense of Observation
Multitasking
Laser Focus on Tasks to be Resolved within a Time Frame
Energetic
Acceptance of Others Differences
Strong Moral Compass
Sustainable Innovation
Website will be constantly updated
"Disneyland will never be completed. It will continue to grow as long as there is imagination left in the world." Walt Disney
© 2024. All rights reserved.


Buy Me a Cup of Coffee
